Cybersecurity Essentials: IT Support Services
In today’s digital age, cybersecurity is paramount for firms of all sizes to protect sensitive data, maintain operational continuity, and safeguard against cyber threats. With the ever-shifting landscape of cyber threats, enterprises must implement robust cybersecurity measures and leverage the expertise of IT support, like Hicksville IT Support, to mitigate risks effectively. In this guide, we’ll explore the cybersecurity essentials that IT support services provide to protect your business from cyber-attacks and ensure peace of mind.
Threat Detection and Prevention
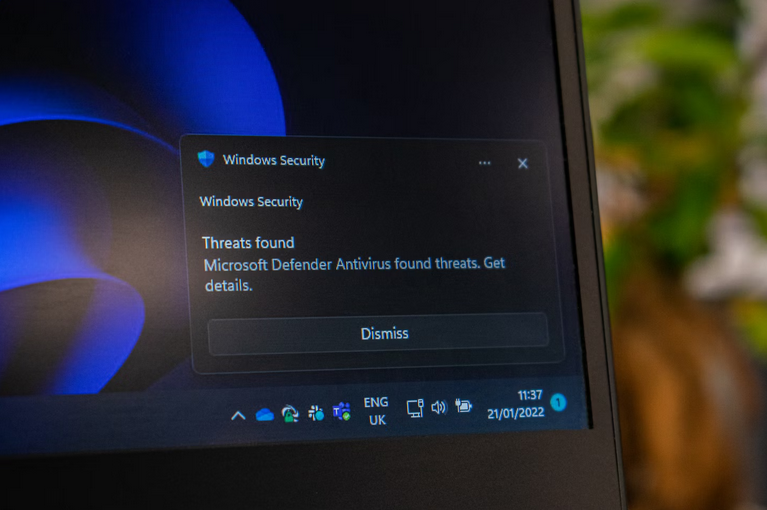
IT support services play a crucial role in threat detection and prevention by implementing advanced security solutions to identify and mitigate cyber threats in real time. This includes deploying intrusion detection systems, firewalls, and endpoint protection solutions to monitor network traffic, detect suspicious activities, and block unauthorized access attempts.
Security Patch Management
Cybersecurity breaches are a substantial risk for enterprises of all sizes, resulting in data theft, financial loss, and brand harm. Updating software and systems with the latest security updates is critical for defending against known vulnerabilities and exploits.
IT support services handle security patching operations by ensuring that software updates and patches are implemented as soon as possible throughout your network. This helps minimize the risk of exploitation by cyber attackers who target unpatched systems to gain unauthorized access or deploy malware. Automated patch management tools streamline the process and ensure comprehensive coverage of all endpoints and devices.
Data Encryption and Access Control
Data encryption and access control measures are essential components of a robust cybersecurity strategy to protect sensitive information from unauthorized access or disclosure. IT support services implement encryption protocols to secure data both in transit and at rest, ensuring that confidential data remains protected from interception or tampering. Access control mechanisms are also implemented to limit access to important data and resources based on user roles and permissions.
Employee Training and Awareness

Human mistakes continue to be one of the primary causes of cybersecurity events. Thus, staff training and awareness initiatives are critical for risk mitigation. IT support services offer cybersecurity training and awareness programs to educate staff on typical cyber risks, phishing scams, and best data security practices. By fostering a culture of cybersecurity awareness inside your firm, employees become better able to notice and respond to potential threats, lowering the chance of security breaches caused by human error.
Incident Response and Recovery
Despite proactive cybersecurity measures, security incidents may still occur, requiring a swift and effective response to minimize the impact on your business operations. IT support services develop incident response plans and protocols to outline the steps to take in the event of a security issue, including containment, investigation, remediation, and recovery. It ensures a coordinated and structured approach to managing security incidents, restoring systems and data, and minimizing downtime and disruption to your business.
In an increasingly synced and digitized world, cybersecurity is a critical priority for businesses to protect against evolving cyber threats and safeguard their assets and reputations. By partnering with IT support services, businesses can leverage expertise, resources, and technologies to implement comprehensive cybersecurity measures that address their organization’s unique challenges and requirements.…



 Technology can streamline recruitment and make it easier for companies to find the best talent. Automation and analytics can help speed up processes such as candidate screening, making it easier for HR teams to identify top talent quickly.
Technology can streamline recruitment and make it easier for companies to find the best talent. Automation and analytics can help speed up processes such as candidate screening, making it easier for HR teams to identify top talent quickly.
 One of the main reasons that many companies prefer VoIP telephone systems over other kinds of systems is that they are cheaper. As a business owner, one of your primary goals is to make money. This may mean cutting down on your operational costs. Although it may not seem like it, a lot of money is spent on communication through the company’s telephone line.
One of the main reasons that many companies prefer VoIP telephone systems over other kinds of systems is that they are cheaper. As a business owner, one of your primary goals is to make money. This may mean cutting down on your operational costs. Although it may not seem like it, a lot of money is spent on communication through the company’s telephone line.
